How Can RASP Security Safeguard Applications in Real-Time Using Runtime Application Self-Protection?
Applications function as the lifeline of digital interactions in the constantly changing world of cybersecurity. Therefore protecting them from a wide range of threats is essential. Traditional security methods frequently fall short when sophisticated assaults at application weaknesses increase. Runtime Application Self-Protection (RASP), which offers a proactive and real-time defense mechanism, enters the picture in this situation. Let’s explore how RASP security may alter how applications are protected by leveraging the power of runtime application self-protection.
Recognizing RASP Security
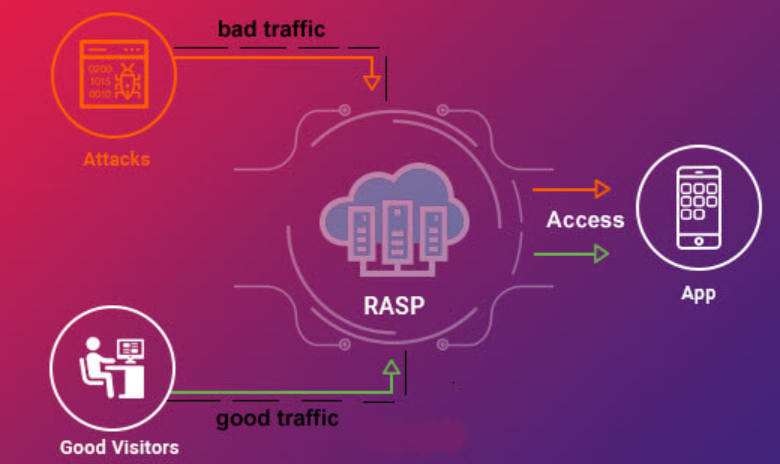
A dynamic security strategy called runtime application self-protection (RASP) addresses the dangers and vulnerabilities that apps encounter when they are in use. Unlike conventional security solutions that operate externally, RASP integrates seamlessly into the application’s runtime environment. Through this integration, the program can continuously monitor its own actions, identify potential risks, and take immediate preventative action.
The real-time protection procedure
Regular observation and behavior analysis
The constant observation of application behavior is the cornerstone of RASP’s real-time security. RASP tracks each action the application takes as it processes data and interacts with users, looking for patterns and outliers from expected behavior. Threat detection is built on a solid understanding of what the application is supposed to do.
Threat detection in advance
RASP is attentive to spotting various dangers, such as code injection, SQL injection, and cross-site scripting. RASP rapidly raises the alarm when anomalous behavior is discovered, warning security teams of potential danger. Real-time detection reduces the window of vulnerability and stops attacks from taking advantage of weaknesses.
Quick mitigation
When a threat is identified, RASP goes beyond simply sounding the alert.; action is taken right away. For instance, RASP can dynamically change the input parameters to ensure that an attempted SQL injection attack is stopped. This practical technique prevents The threat from spreading further inside the application.
Zero-Day Vulnerabilities Protection
Zero-day vulnerabilities, used against software before the vendor is even aware of them, present a severe problem. RASP’s real-time monitoring and preemptive response are beneficial in dealing with such vulnerabilities. RASP can provide a robust defense against new threats by analyzing behavior and spotting abnormalities pointing to an unknown threat.
Adaptive Learning
Staying ahead of changing threats in the dynamic field of cybersecurity calls for more than just static defenses. Applications need a proactive strategy to adjust to shifting attack vectors because they are attractive cyberattack targets. In the context of Runtime Application Self-Protection (RASP) security, the idea of the adaptive learning process is relevant.
Explicitly Defining the Adaptive Learning Process
RASP security uses an adaptive learning method that dynamically modifies security measures in response to real-time insights gathered from application behavior. This learning process is a continuing process of honing threat detection and response tactics, not a one-time event.
Stages of the Adaptive Learning Process:
Data Collection
The ongoing gathering of data from an application’s interactions with users, other systems, and data sources is the foundation for adaptive learning. The application’s expected behavior is deduced from the detailed observation of each transaction, input, and response.
Creating a behavioral baseline
RASP sets a baseline of typical behavior using gathered data. The baseline serves as the standard by which deviations are evaluated. It includes user behavior patterns, data flow patterns, and system responses that are normal for the program.
Abnormal Findings
RASP’s aptitude for analysis is used as the adaptive learning process develops. Potential anomalies are signaled when there are differences from the established behavioral baseline. Then, these abnormalities are examined more closely to see if they point to malicious activities or legitimate shifts in application behavior.
Constant Improvement
The repetitive nature of adaptive learning is what makes it so beautiful. The learning process continues after an anomaly is identified and determined to be non-threatening. Instead, RASP uses this knowledge to improve its comprehension of typical behavior. This improvement reduces erroneous warnings and enhances the system’s capacity to differentiate between severe dangers and harmless variations.
Response Improvement
RASP’s threat response tactics are improved with each cycle of adaptive learning. As a result, RASP improves its ability to detect anomalies and launch appropriate reactions. For instance, it can create more subtle tactics to counter new dangers.
Benefits of the Adaptive Learning Process
Static security methods must frequently catch up in the never-ending fight against constantly changing cyber threats. It is where Runtime Application Self-Protection (RASP) security’s adaptive learning mechanism shines as a game-changer. The adaptive learning process offers many advantages that raise application security to new heights by encouraging ongoing growth and refinement.
Continuous Development and Improvement
The idea of continual evolution is arguably the most crucial advantage. The adaptive learning process is a constant process of development, not a one-time project. As a result, an application’s security posture continuously develops, keeping up with attackers and their innovative techniques.
Changing Environments: Adaptation
The adaptive learning method enables programs to adapt to changing settings in a fast-changing digital landscape. The application’s security methods stay applicable and effective when user behaviors change and the application’s functionalities increase, ensuring complete protection.
Improved Response Techniques
The adaptive learning process promotes ongoing learning and improvement, which results in the creation of more complex response strategies. An application’s ability to dynamically counter threats becomes more complex and effective, which increases the success rate of preventing attacks.
Optimized Resource Usage
Resources are allocated more effectively as the program gets better at differentiating between normal and abnormal behavior. Security teams can concentrate on dealing with actual risks by streamlining their operations and ensuring that resources are used where they will have the most significant impact.
Integration that is seamless and has minimal performance impact
The possible influence of security measures on application performance is one issue. RASP takes care of this by smoothly integrating into the program’s runtime environment. The application’s user experience won’t be threatened by security thanks to this integration’s little performance overhead.
Conclusion
Applications are the means of conducting business, communicating, and exchanging data in the digital age; thus, protecting them from dangers is crucial. Runtime Application Self-Protection (RASP) security stands out as a formidable option in this effort. RASP redefines application security by combining the power of real-time monitoring, proactive threat detection, quick mitigation, defense against zero-day vulnerabilities, adaptive learning, and seamless integration. Applications can become more than simple tools; they are vigilant defenders of data and functionality, creating a safer online environment for both users and organizations.